Breathtaking Info About How To Detect Denial Of Service Attack

1 you can use the netstat command on your machine to see all network connections from your computer to any external host.
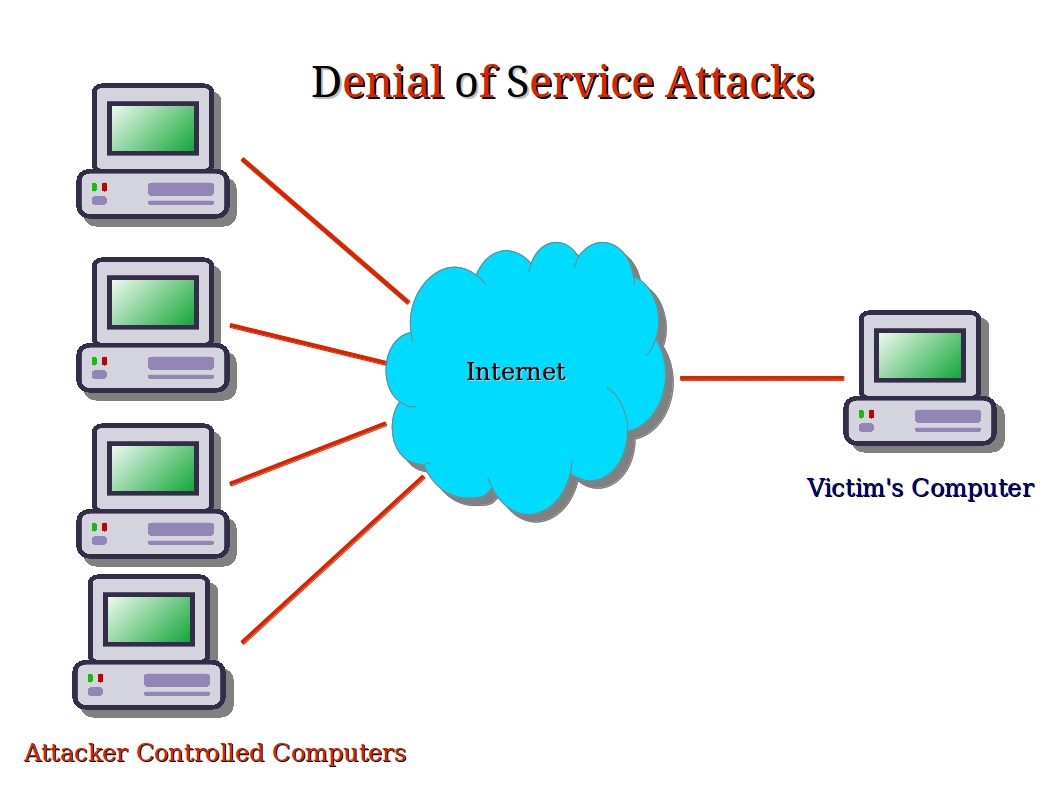
How to detect denial of service attack. Different types of dos attacks what is the difference between a ddos attack and a dos attack? A denial of service attack can be carried out using syn flooding, ping of death, teardrop, smurf or buffer overflow. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
If the number of requests rises above the capacity limit, the. Resource depletion is a common attack vector, where limited system resources (e.g. 56 ( 2022 ) cite this article 20k accesses 16 citations metrics abstract currently, distributed denial of service attacks are the most dangerous cyber danger.
You can create alerts for anomalous traffic, uncover traffic sources or block and log. Detecting denial of service attacks using machine learning algorithms kimmi kumari & m. Also, consider services that can disperse the massive ddos traffic among a network of servers.
A cellular outage thursday hit thousands of at&t users in the united states, disrupting calls and text messages as well as emergency services in major cities including san francisco. If the number of requests rises above the capacity limit, the. However, another sign of a ddos attack is a very strong spike in bandwidth.
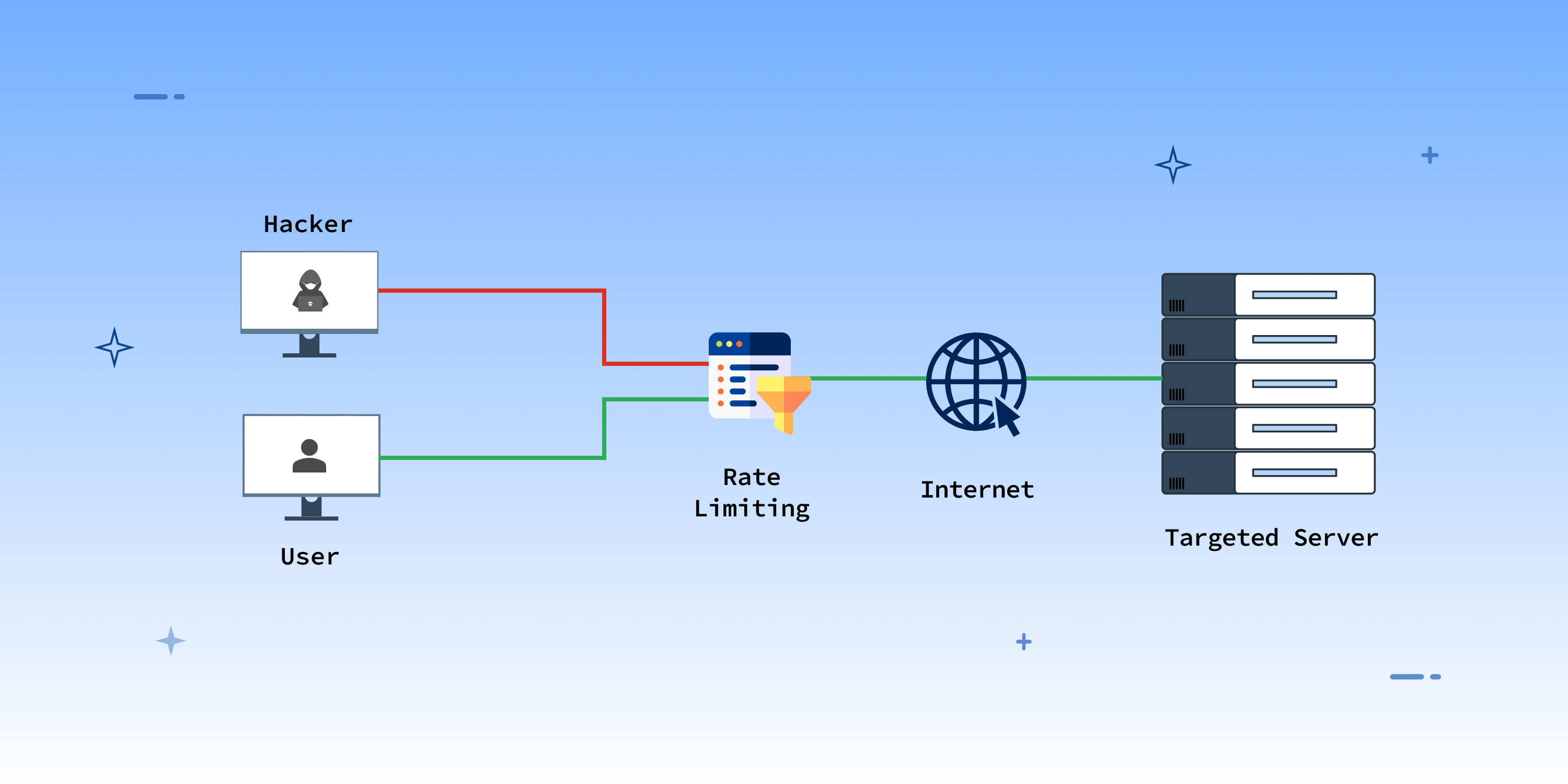
Denial of service (dos) type network attacks attempt to make network services inaccessible by overloading them with maliciously generated traffic. Typically, in this attack, multiple systems overload a. By leveraging a firewall or intrusion detection system, you can audit network traffic.
Services affected may include email, websites, online accounts (e.g., banking), or other services that rely on. Dos attacks use two primary strategies to accomplish that goal. Ddos attacks, a subset of dos, use multiple compromised systems for a broader impact.
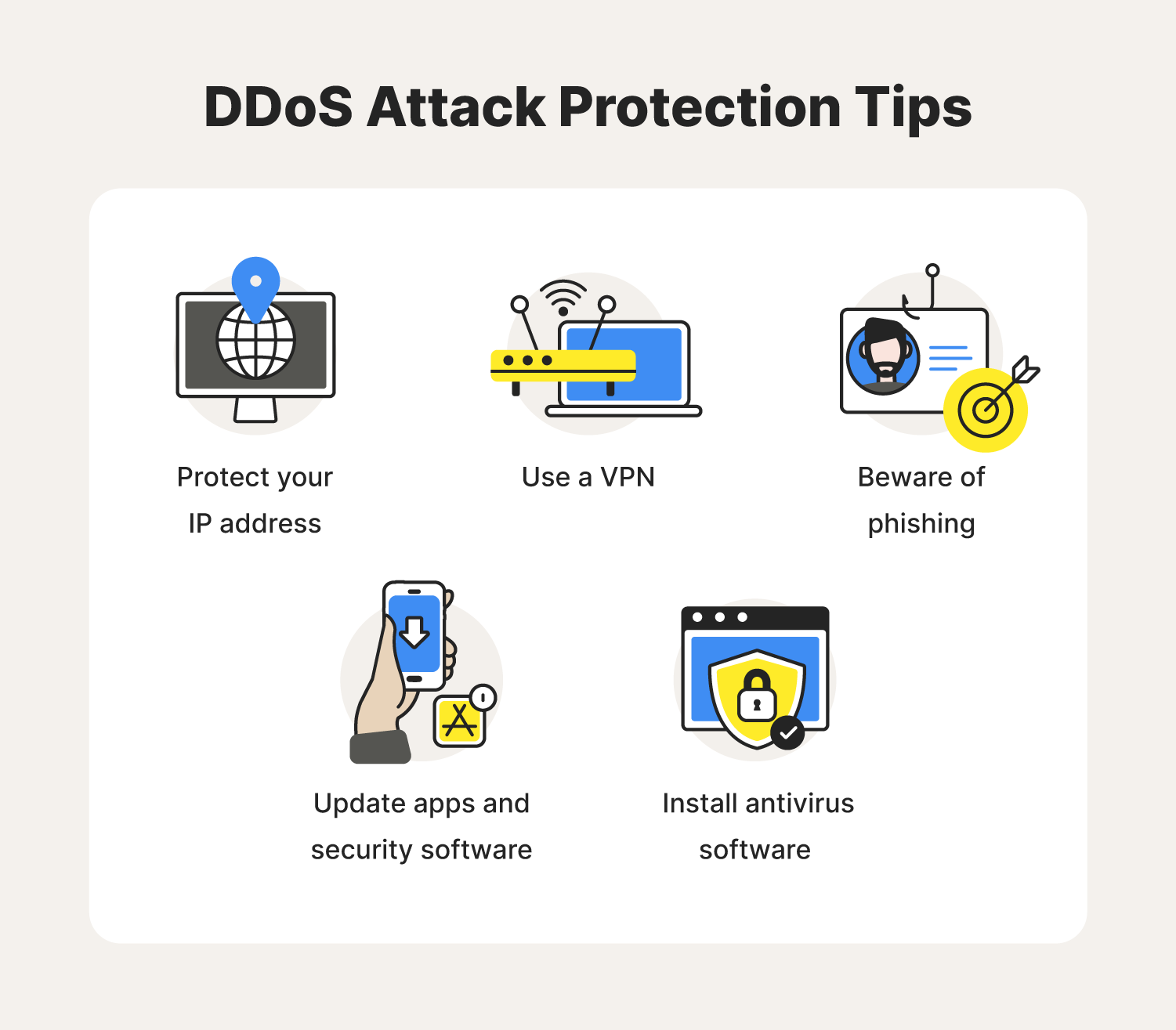
Dos attacks can be categorised in different ways, but the attacker's main aim is to target. Before diving into the specifics of detecting and mitigating dos attacks with microsoft sentinel, it is essential to understand the nature of these attacks. If you find your company is under attack, you should notify your internet service provider as soon as possible to determine if your traffic can be rerouted.
Why do denial of service attacks exist? Mrunalini journal of big data 9, article number: When such an attack is carried out with the contribution of many sources, the attack is called a distributed denial of service (ddos) attack.
There are two types of attacks, denial of service and distributed denial of service. 3 answers sorted by: Memory, cpu, disk space) are intentionally “used up” by the attacker in order to cripple the target’s normal operations.
Techniques like syn flood, teardrop, icmp flood, and buffer overflow exploit vulnerabilities to crash servers. Learn more about cloudflare's ddos protection and how it works. How do you know if your website just went down because of a ddos attack?